Managing business and export risk
No business is immune from cyber risk. Whether you’re big or small—or somewhere in between—the risk of a technology failure, cyber attack or breach exists. What’s more, the costs and stakes are high.
Chapters
Stay secure - Cyber risk
In this chapter
- 5.1 Cyber risk - what you need to know
- 5.2 Why play for cyber risk?
- 5.3 Cyber risk 101: how attacks happen
- 5.4 Cyber risk and data privacy
- 5.5 Get smart or be out-smarted
- 5.6 Expert insight: the cost of cyber security
- 5.7 6 steps to better cyber security
- 5.8 Questions every company should ask about cyber risk
- 5.9 Cyber risk resources
No business is immune from cyber risk. Whether you’re big or small—or somewhere in between—the risk of a technology failure, cyber attack or breach exists. What’s more, the costs and stakes are high. The global average cost of a data breach is US$3.62 million, according to the 2017 Ponemon Cost of Data Breach Study. Each lost or stolen record containing sensitive and confidential information is equivalent to US$141. That can add up quickly regardless of the size of your business.
Case in point: the Equifax data breach of 2017. Considered the largest in history, it compromised the personal data of 247 million people and cost the company $439 million, only $125 million of which was covered by insurance.
What is cyber risk?
Cyber risk, or technological risk, is any risk of financial loss, disruption or damage to your business resulting from an information technology (IT) failure or attack. This could involve
- intentional security breaches
- accidental or unintentional breaches
- IT threats stemming from poor systems or technology failure
The best way to manage cyber risk is to plan for it—and have a strategy in place that will help you deal with an attack, breach or failure when it happens. Your plan should include scenarios involving breaches or failures that affect your supply chain partners, too.
As our dependency on electronics and devices grows, so too does our need to anticipate and prepare for the risks that come with it, including:
- Internet of Things (IoT)
The IoT refers to any standalone device, including computers, phones, cars, music systems and even kitchen appliances that connect to the Internet—and to each other, often remotely. These devices can be monitored or controlled from a remote location. By 2020, the number of connected devices is expected to reach 200 billion, according to research by International Data Corporation, a global research firm. - Dependence on digital technology
Technology is now integrated at all levels of our business operations. This leaves businesses and global supply chains vulnerable to a range of risks. From mobile devices to automated processes, cloud services, security monitoring and more, technology disruptions can range from frustrating to critical. - Human behavior
Employees are often the weakest link when it comes to protecting your company. Their errors can range from simple ones, such as sharing a password or clicking on a link in a spam email, to big ones like intentionally sharing or leaking sensitive company information. The PricewaterhouseCoopers (PwC) Canada Global State of Information Security Survey 2018 reported that 63% of Canadian business leaders say employees—both past and present—were the probable source of cyber breaches. - Legislation
In Canada and internationally, your company is subject to laws that govern how you manage and protect data. Organizations that do not safely collect, protect and destroy data leave the door open to huge costs. Yet between 2010 and 2018, data breaches exposed the identities of more than 7.1 billion users, according to the MMC Cyber Risk Handbook 2018.
There are 4 primary ways criminals and competitors might attack your company. Keep in mind that attackers are often sophisticated and almost always looking for your point of weakness. For many companies, this means directing the attack at an unsuspecting employee. The human factor is every company’s biggest risk area.
- Ransomware
Ransomware uses a computer virus to encrypt your data and hold it hostage. Usually, the virus attacks when a user clicks on a link or attachment. The ransomware locks you out of your files, and without a proper backup strategy, you are at the mercy of your attackers. Their motivations range from collecting ransom money to disrupting your business. - Phishing
With phishing, an attacker pretends to be a reputable company or person. Their aim? To fish for (and eventually gather) information such as login credentials, passwords, credit card numbers or account information. In a phishing scam, someone in your company clicks on a link in an email, giving the scammer access to your files, intellectual property, money and more. - Privacy breaches
In the case of privacy breaches, your attacker is interested in one thing: gathering as much data from you as possible. They may be working for your competitor or collecting information to share on the dark web. - Infiltration
Your competitor or cyber criminals may infiltrate your business using malware and other technology. Their objective? To get anything of value or cause you harm—or both. In these cases, they may harvest data, get access to valuable intellectual property and trade secrets, or control industrial equipment, lighting systems or any other connected devices.
Protecting data privacy is paramount, so it’s important to build it into your risk management plan. Your company may handle a lot of information—from credit card numbers to addresses, health information and other confidential data—and you are legally required to keep this information safe.
Canadian laws
New Canadian legislation related to personal data in 2018 will require that companies report data breaches to the Office of the Privacy Commissioner of Canada. The Personal Information Protection and Electronic Documents Act requires that private sector organizations notify anyone affected by a breach. Failure to do so could result in fines of up to $100,000 under the legislation.
The new law details how Canadian businesses must report breaches, and to whom, including the steps you must take to notify individuals who have had their data compromised. As well, companies and organizations must do everything in their power to ensure that users’ personal information is kept safe.
Canada’s provinces also have laws around personal data protection, including health data.
European Union laws
In May 2018, a new European Union (EU) law with global impact came into effect. Called the General Data Protection Regulation (GDPR), it requires companies to comply with it, no matter where their head offices are located.
If your company uses the personal information of any EU citizen in any way, the GDPR applies to you.
GDPR consists of several data protection rules that require companies and organizations to put users’ rights first. The rules include:
- Disclose who you are and how you will use the person’s data, using clear language
- Obtain clear and direct consent from all individuals
- Within 3 days of a serious data breach, report fully to clients
- Delete data when a user requests it
- Give users access to their data; they can transfer it elsewhere
The penalties for not complying with this law? You could be fined 4% of worldwide annual sales, to a maximum of €20 million (CAD $30 million).
Big or small, every business needs to prepare for the risk of cyber attack or failure.
Information technologies are so crucial to so many parts of your business that a breach or virus can mean disaster. And it’s not just hardware or software that can crash. The global infrastructure of information that swirls around us 24/7 requires constant monitoring and managing. So, what do you need to know?
- Threats vary
Your business might survive 48 hours without email, but how will it recover from the public release of confidential customer data? It’s important to define and prioritize cyber risks based on their potential impact on your company. - Beware of myths
Is cloud-based software as risky as an independent software supplier wants you to believe it is? Do your homework before you decide what is truly a risk, or before you dismiss a new threat that you do not fully understand. - Dominos crash
What if an important company in your supply chair suffers a cyber attack, breach or failure? Your cyber risk plan needs to consider things that go wrong elsewhere but have a direct impact on you. - Social media matters
How are you managing your social media presence? Your company should only trend on Twitter because you want it to trend. Every company needs a social media policy and professional staff to manage this potentially damaging corner of cyberspace. - Protect your brand
Do you have intellectual property or trade secrets that someone is stealing or using without your permission? Insurance can help you recover costs linked to devaluation of intellectual property. Make sure you’re covered for the types of cyber attack that will put your company at the greatest risk.
“Proper cyber security does not have to be expensive. It has to be smart. Your company may invest heavily in your IT infrastructure and pass compliance with flying colours. That doesn’t mean you’re secure. There’s always the human factor—and humans can easily be fooled. The best way to address the issue is through ongoing training and awareness.
It’s also important to conduct regular external third-party audits. This means hiring a cyber security firm to try to penetrate your environment and tell you exactly what the bad guys can do to you. Every $1 you spend on being proactive is equivalent to $12 spent reacting to a breach. So, get your house in order and have a plan. When an attack happens, don’t panic and try to fix it yourself. This makes it difficult for a cyber expert to investigate the source and stop the bleeding.”
-Daniel Tobok, CEO, Cytelligence
Internationally recognized cyber security and digital forensics expert
By taking the right approach, your business can deal with cyber risk as effectively as you deal with other risks. Increase your risk effectiveness by following these 6 steps.
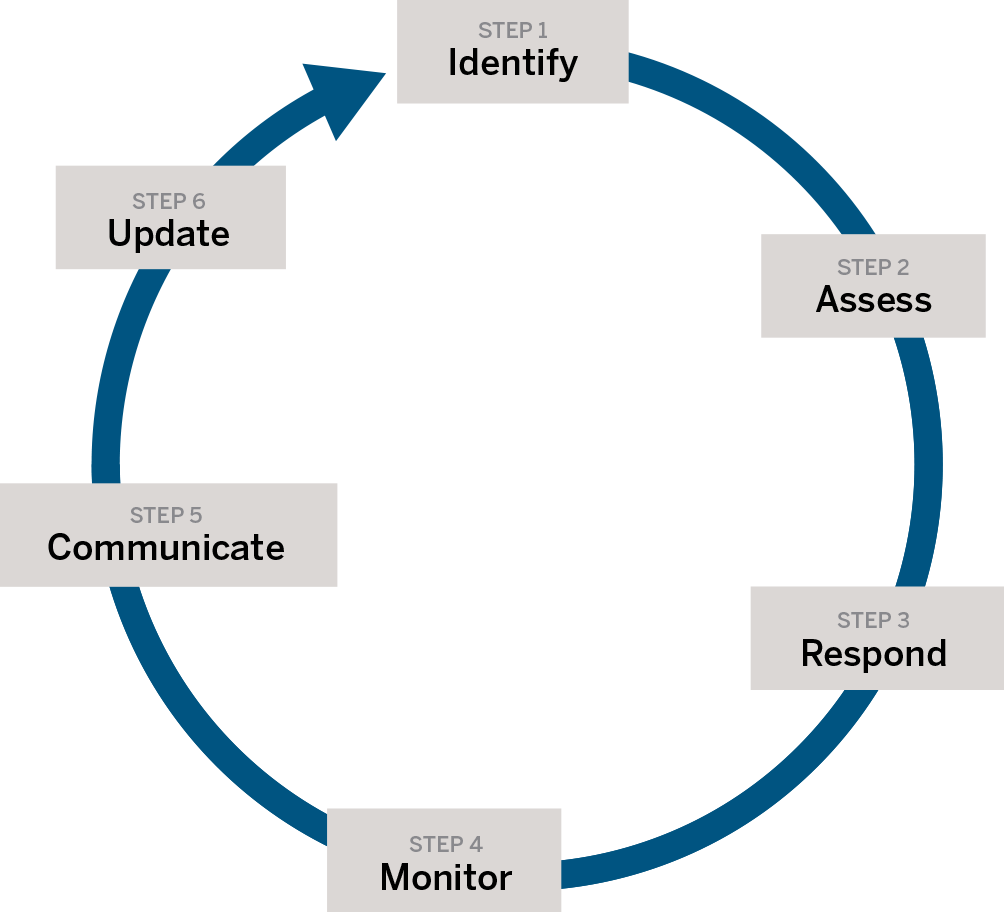
STEP 1:
IDENTIFY your company’s most vital cyber and information assets. Involve senior management to ensure they understand and work to mitigate cyber risk, at all steps along the way. Schedule time for your team to identify the main issues that make your company vulnerable to attack or failure.
STEP 2:
ASSESS your security gaps. Hire a cyber security firm to audit your systems and infrastructure. Based on their findings, set priorities for achieving a higher level of cyber security. Do you need to enhance security with a few tweaks, or to overhaul your information systems, training and policies.
STEP 3:
RESPOND to cyber risks in a comprehensive and timely way. Develop and implement a cyber risk plan that will safeguard your company’s reputation, data and intellectual property. Your plan must also consider the harm a cyber attack might do to your customers and supply chain partners. Hire staff (or a cyber security company) to guide you. Finally, educate senior management so they know the response plan.
STEP 4:
MONITOR cyber threats and review your cyber risk plan as regularly as you look at quarterly profits. Yes, it’s that important.
STEP 5:
COMMUNICATE the business impacts of cyber risk throughout the organization. Make sure decision-makers are aware and informed, on an ongoing basis, about existing and potential cyber risks. Develop and implement an employee training and awareness program so they understand cyber risk and their role in keeping your business safe.
STEP 6:
UPDATE your response protocols every time you test them. Update your cyber risk plan as often as needed, and on a schedule that allows you to identify and deal with new risks. Stay committed to adapting often.
Cyber risk oversight
- Who in the company is responsible for managing cyber risk?
- Which senior executive is the lead on this topic? Who keeps them informed?
- Is cyber risk fully integrated into the company’s larger risk management framework?
- Do you know and apply the laws that relate to privacy and data security?
- Is the company investing as much as it should to mitigate cyber risk?
Cyber security impacts
- What impact will an attack have on your company’s reputation? Market value? Competitiveness? Liability?
- What expectations do customers have that you will safeguard their personal data? What are your legal obligations?
- Do any supply chain partners present a cyber risk that you should be mitigating?
- Are all your IT systems operating at high levels of security?
Corporate response
- Do you have a cyber risk incident response plan? Has your company tested and validated it?
- Have you hired a cyber security firm to try to penetrate your environment and test your weak points?
- Who is in charge of alerting the company to a cyber attack or breach?
- Do you have the proper patch systems in place to deal with ransomware and other forms of attacks? Do you regularly back up your files on a hard drive?
- Do you have systems in place to manage the aftermath of a cyber attack (setting up customer help lines and using social media to update customers)?
- Do you have cyber risk insurance to help cover costs related to an incident?
Training and Awareness
- Does your company have a plan to educate employees about cyber risk?
- Do you have an awareness program to ensure employees are regularly updated about emerging risks and reminded about malware, phishing scams and other common forms of attack?
- Who receives cyber risk training to prepare your company for mounting a response? How often is the training upgraded and reissued?
The following resources provide additional insight and information to assist with your cyber risk planning.
- EDC’s 3-part series on Cyber Risk Management has excellent information to help you to plan for and manage cyber risk.
- The Ponemon Institute’s 2017 benchmark study, Cost of Data Breach Study: Global Overview, offers insights into the cost of data breach incidents for companies.
- The Canadian Underwriters offer a good overview of the 2018 changes to Canadian privacy legislation in the blog post, Digital Privacy Act Changes are Coming: Are You Prepared?
- The European Commission’s 2018 Reform of Data Protection Rules web site has everything you need to know about the new GDPR rules for businesses and what you can do to ensure you comply.
- The MMC Cyber Risk Handbook 2018 highlights shifting and emerging cyber threats, and provides information on global regulatory trends and building better cyber resiliency.











